To quote from the immortal words of Terry A. Davis, “The computers went wrong when you made them for niggers, that’s when it went wrong. […] The white people are like ‘it’s a command line what’s your point?’ The niggers are like, ‘no we don’t like a command line’. Here’s the difference between a white man and a nigger, ‘Do you like a command line?’ Ok, fuck you. Get out.”. And that’s why Steve “Definitely doesn’t have AIDS” Jobs invented the GUI. Or at least that’s what apple fanboys will tell you.
The fact is Microsoft and Apple dominated the personal computer scene with general purpose operating systems or in apple’s case, more so tailored toward their machines which are sold like faggy fashion accessories. And to all you unix fanboys, OSX continues to be unix certified to this day. The problem is with proprietary software. One example is _NSAKEY, a variable discovered in windows NT back in 1999. Microsoft did a PR coverup saying the variable name came from the fact the NSA is the technical review authority for cryptography export controls. However more investigation just led to even more puzzling keys being discovered in the operating system.
It’s no coincidence why PGP was classified as a munitions export for a while. The only reason PGP is used so widely now by non-governmental organizations is munitions export bans were evaded by publishing the source code as a book. Cryptography and the idea of personal privacy and security is what gave birth to the cypherpunk movement. It was ultimately just a mailing list, with al-qaeda.net being a node for example, rather than a cohesive movement, but its adherents did achieve numerous societal changes. The government has been trying to subvert security and encryption standards for longer than a lot of readers have probably been alive. For instance, when SSL was created and seemed qualified to be infeasibly unbreakable when implemented/used correctly the US was brokering cryptography export deals on far weaker 40-bit RC2 and RC4 encryption. There was also a scheme to use a cipher called Skipjack, which was to be implemented in a device promoted by the NSA called the clipper chip which would supposedly secure voice and data messages. It was a cypherpunk mailing list adherent Matt Blaze that found a serious flaw in its implementation and hastened the demise, at least right then, in the government backdooring private communications. It should be no surprise he now is on the board of directors for the tor project given his commitment to privacy and security.
Intelligence agencies have made attempts to backdoor encryption for years. Sometimes even going so far as to find exploits in software and not disclosing them in order to use them for personal ends. Fallout from that can be seen from the leak of NSA hacking tools by the Shadow Brokers group. The most well known leaked exploit is eternalblue, as that was the exploit used by the wannacry cryptoworm which ranks it in the top 5 for most economically destructive computer viruses of all time. Considering all its predecessors were developed in the early 2000s and wannacry was released in 2017 that is impressive. All intelligence agencies do this and what is today’s zero day is tomorrow’s hacker’s tool and next week’s script kiddy toy. The eternal blue exploit itself was in Microsoft’s implementation of the SMB protocol.
This brings me back to my main point. If you value personal privacy and security, you should use linux. It dominates the supercomputer and server world for a reason. If you have adware on your personal computer you might lose some computing resources and be mildly inconvenienced, but malware on important servers or computer clusters would be extremely detrimental. Linux is open source and licensed under the GPLv2 meaning it is really free and open source. The license is in effect a copyleft license, which works like a virus meaning any derivative work from GPL licensed and freely accessible source code must also be GPL licensed. This is contrary to permissive licenses like the BSD license used by projects such as the various BSDs in existence today. It’s why apple is free to use their code and implement as much proprietary telemetry and spyware on top as they wish. Given the diversity of linux operating systems and their inherently better security (such as getting software from signed repositories rather than russianmalware.ru/gamehax) your privacy and security are likely guaranteed. There is of course linux malware, but most target servers as that’s where the real money is. No one cares about whatever fraction a percent the linux desktop user markershare holds.
The FOSS model also makes it a lot harder to implement malware in the linux ecosystem. There’s been attempts on behalf of researchers and likely a few unconfirmed attempts by the government itself. The government has even approached Linus Torvalds (developer of linux) directly to implement a backdoor. It should be telling however that the NSA itself even developed security-enhanced linux themselves (essentially mandatory access control policies that’d make sense for an intelligence agency).
It should be noted that other countries are following suit. Astra linux is a Russian developed linux operating system for its armed forces and intelligence agencies given western provided proprietary operating systems simply would be detrimental to national security. Even the North Koreans have their own linux distribution, Red Star OS, although it by design wasn’t made for the privacy of its citizens if you look more into it. In cooperation with the PRC Ubuntu even developed and released Ubuntu Kylin as a loose continuation of Kylin OS. Kylin itself was originally based on freebsd, but later linux (hence it’s rebranding to NeoKylin). 90% of the market share in the government sector is held by either Kylin or NeoKylin, while Ubuntu Kylin is marketed for domestic computer users.
Why then, aside from the highly convincing Terry A. Davis quote given at the start and obvious insinuations that foreign powers seem to have a reason to distrust American corporate firms who have been shown to be in bed with the government ever since the Snowden leaks and before, should I switch to Linux? Simple. It’s free and open source and has a wide decentralized amount of support. When I mentioned researchers and the government likely tried to implement backdoors into linux, it was because of the scrutiny of FOSS contributors that spotted the bugs and prevented them from being merged with the mainline kernel. Furthermore, most linux systems use a variety of GPL licensed tools such as the various GNU utils, although there are distributions like alpine linux that intentionally avoid GNU utils for reasons too autistic to get into in this article. Point being, there’s a billion linux distributions for just as many use cases. If you are a full blown schizo consider qubes, then just wrack your brain at night thinking of hardware level backdoors. For instance a lot of drivers especially wireless ones require proprietary blobs and it is likely your CPU itself is running a stripped down minix system itself which functions as a blackbox, but makes an educational unix-like operating system into the most widely used operating system in the world without the creator even being made aware or too pleased. There are tools such as coreboot and libreboot, but it only really gimps INTEL ME although you may still be able to entirely thanks to a backdoor left by the NSA itself. There’s been demonstrated attacks using firmware in other hardware as well which is especially easy with missing or incorrectly implemented IOMMU.
The scary thing about mass surveillance is when you become self aware of it and try to distance yourself from it your traffic raises flags. A linux forum was once enough to get you on an NSA watchlist. As was visiting the tails website. Ever notice how even with VPN on with most default configuration your DNS is being “encrypted through cloudflare”. I’d call it more of a man in the middle attack. Seem familiar?
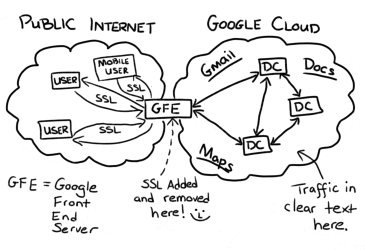
How then can you become secure against a state actor? Well, try not to be a target. That’s my best suggestion. Otherwise, use open and well audited protocols and self host rather than relying on commercial services. Openvpn is a protocol, nordvpn is a for profit company, and there’s a big difference. That’s also why tor nodes are run by volunteers and why governments try to compromise the security of tor through misinformation campaigns and trying to control most exit nodes. What I’m trying to say is, learn to use tools properly but also know their limitations. And avoid proprietary software whenever possible. It’s better to be paranoid and right then oblivious and in jail, or worse. Oh and of course, watch our dear prophet Luke smith on the youtube frontend https://vid.puffyan.us/feed/popular or a FOSS desktop app such as https://freetubeapp.io/ as well as the honorary Aryan mental outlaw. They should guide you on your path to schizo-enlightenment. Oh and use suckless software if you are a true nazi.

